 Andreas Thies and I have just had accepted a paper for publication at this year’s ISSTA. I have just put our camera-ready copy online. We describe an approach to ensuring the correctness of refactorings for Java programs that use reflection:
Andreas Thies and I have just had accepted a paper for publication at this year’s ISSTA. I have just put our camera-ready copy online. We describe an approach to ensuring the correctness of refactorings for Java programs that use reflection:
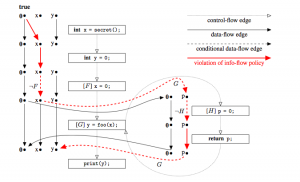
If programs access types and members through reflection, refactoring tools cannot guarantee that refactorings on those programs are behavior preserving. Refactoring approaches for highly reflective languages like Smalltalk therefore check behavior preservation using regression testing.
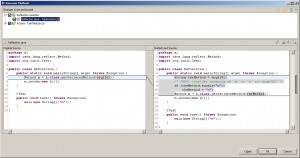
In this paper we propose RefaFlex, a novel and more de- fensive approach towards the refactoring of reflective (Java) programs. RefaFlex uses a dynamic program analysis to log reflective calls during test runs and then uses this in- formation to proactively prevent the programmer from exe- cuting refactorings that could otherwise alter the program’s behavior. This makes re-running test cases obsolete: when a refactoring is permitted, tests passing originally are guar- anteed to pass for the refactored program as well. In some cases, we further re-write reflective calls, permitting refac- torings that would otherwise have to be rejected.
We have implemented RefaFlex as an open source Eclipse plugin and offer extensions for six Eclipse refactor- ing tools addressing naming, typing, and accessibility issues. Our evaluation with 21,524 refactoring runs on three open source programs shows that our tool successfully prevents 1,358 non-behaviour-preserving refactorings which the plain Eclipse refactorings would have incorrectly permitted.