With the help of our new CodeInspect tool, we – together with the McAfee Research Lab – have identified a new threat campaign currently underway in South Korea;
attempting to exploit the huge media frenzy surrounding the release of the movie ‘The Interview’.
Shortly after the news broke that The Interview, originally scheduled to be released on Christmas Day, would appear online from Sony Pictures, numerous sites claimed to offer a pirated copy–fueled by the rumors that the movie might be distributed free online due to the circumstances surrounding the film’s change in distribution. One claim making the rounds in South Korea turned out to be an Android Trojan we have designed Android/BadAccents (named after the main component in the first stage of the Trojan).
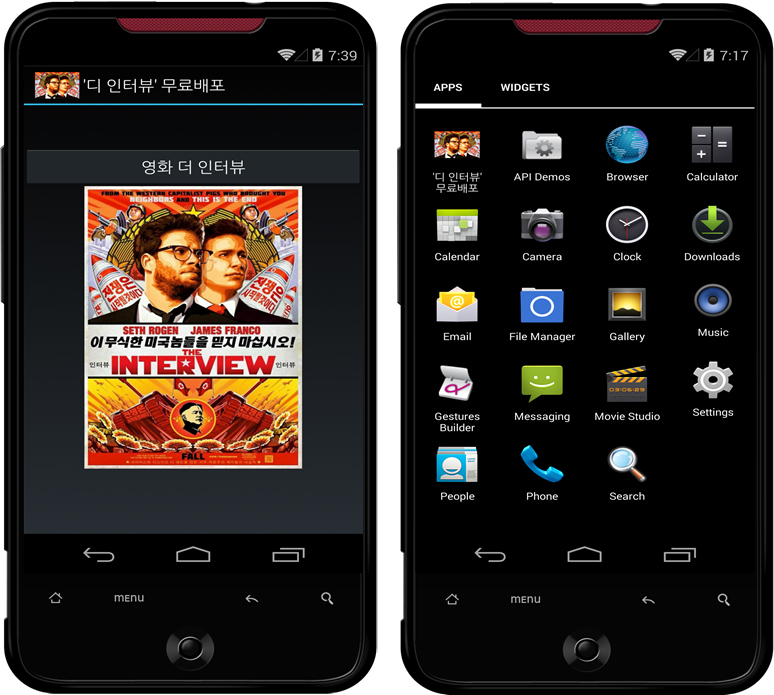
Android/BadAccent claims to download a copy of The Interview but instead is the first-stage downloader of a two-stage banking Trojan. The second-stage component, which was distributed using Amazon Web Services, targets account holders of prominent local banks in South Korea as well as one international bank.
One element of the threat’s code caught our attention: the presence of a detection routine that checked the device manufacture before infecting the device. We had at first overlooked this because we had not heard of the manufactures Samjiyon or Arirang; we later found they are not located in South Korea. If the device manufacture was set to either 삼지연 (Samjiyon) or 아리랑 (Arirang ), then the threat would not infect the device and instead prompt the user with a message that an attempt to connect to the server had failed, as we see in the following image.
When installing on any other brand of device, the infection is completed immediately following the download and execution of the second-stage payload.
Currently we don’t believe that this is a politically motivated threat–limiting the infection to devices sold only in South Korea–but purely a business strategy. Because the malicious payload targets account holders in South Korea, why waste bandwidth on an audience outside of the country?
Using the new specialized tool CodeInspect developed by the Secure Software Engineering Group at CASED, the joint IT-security research center between Technische Universität Darmstadt and Fraunhofer SIT, we were able to decrypt the account information that was used by the malware’s authors to relay information to a mail account hosted outside of South Korea.
Despite the fact that this campaign appeared to be relatively new when we discovered it, the number of infected devices that relayed data was about 20,000. Because accounts related to this threat are hosted outside of South Korean, authorities cannot easily dismantle the campaign and prevent further infections. This tactic has become very popular with threats targeting mobile devices in Korea.
Our investigation of the second-stage component indicates that the malware’s components as well the Amazon Web Security services may have been used in previous campaigns targeting banks in South Korea as early as October. McAfee has notified Amazon Web Security and the Korea Internet & Security Agency of our findings. We are working with them to stop the distribution and prevent further infections of this campaign.
The post Fake “The Interview” App Delivers Mobile Malware in South Korea appeared first on McAfee.
Very soon, in a second post on this topic, we will take a deep technical dive into the code and tactics used in this campaign.
Also other media have reported about it:
Cross-posted from SEEBlog









