Fraunhofer research fellow selected for the Grand Finals of the »ACM Student Research Competition 2016«
For her contribution to this year´s Student Research Competition of the »37th annual ACM SIGPLAN conference on Programming Language Design and Im-plementation (PLDI)«, a Fraunhofer research fellow scored first place in the PLDI Student Research Competition, and is therefore selected for the Grand Finals of the »ACM Student Research Competition.«
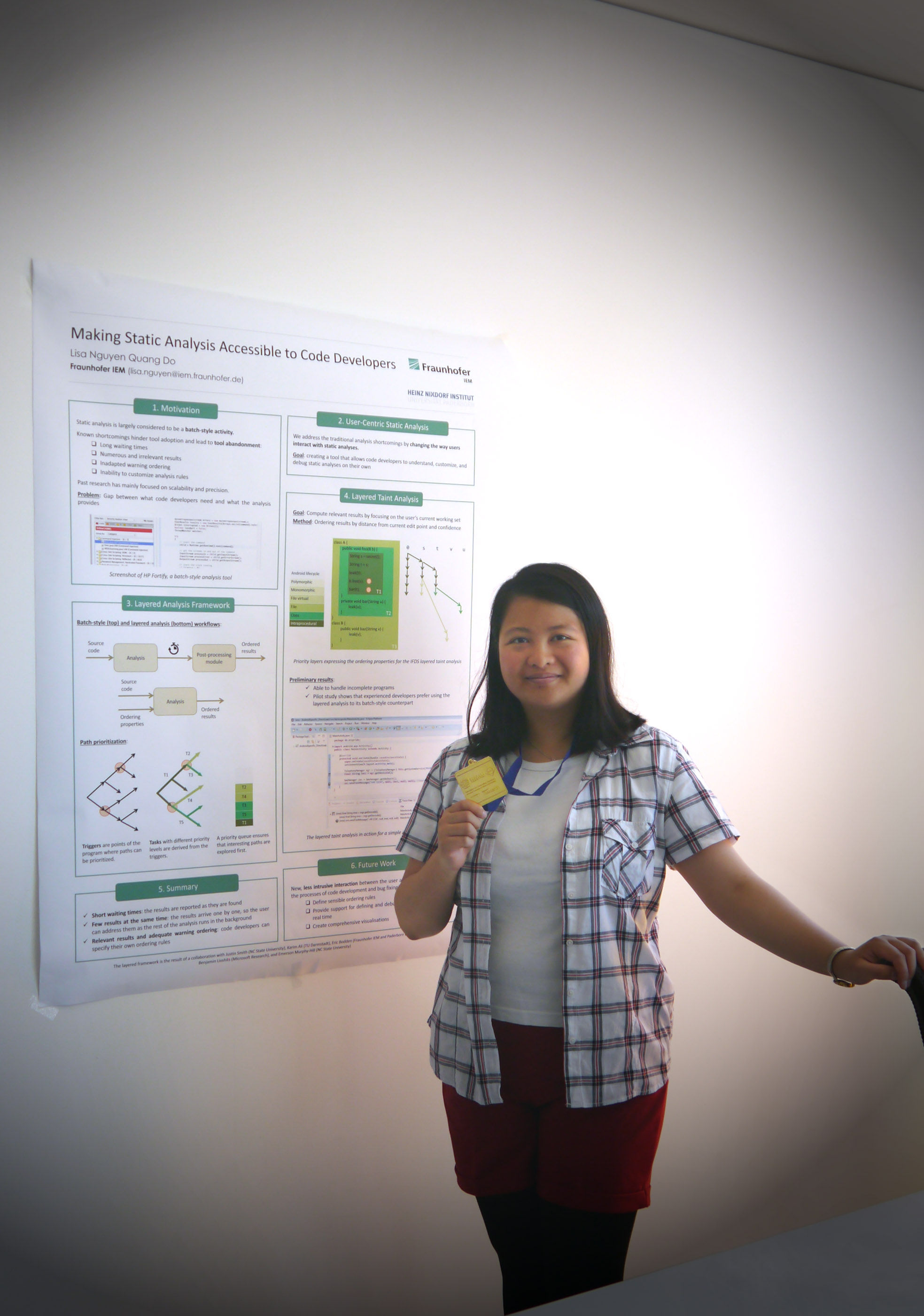
In industrial settings, static analysis is widely used to ensure code quality and security. It is still largely considered to be a batch-style activity, where code developers run static analysis tools, wait for it to finish, and then examine the results. This process often takes hours to complete, prompting development teams to run static analysis tools as part of nightly builds. During this time, the code often has evolved further, causing some errors to be obsolete already when they are reported. Additionally, end-user experience shows that developers have to deal with numerous results, and spend considerable effort in sorting false positives and prioritizing the warnings they would correct. The classification techniques offered by many tools allow developers to have a better overview of the analysis results, but the problem remains that an analysis is still treated as a black box, and software developers have a limited influence and understanding of what the analysis finds, and why it finds it.
Thien-Duyen Lisa Nguyen Quang Do, research fellow at Fraunhofer IEM (Department Software Engineering, Prof. Dr. Eric Bodden), researches the field of User-Centric Static Analysis. She advocates that static analyses should be able to accommodate specific users’ requirements about the behavior of the analysis in specific situations.
One of her ideas towards this goal, in collaboration with TU Darmstadt, Paderborn University, Microsoft Research, and NC State University, introduces a layered analysis framework in which the developer can explicitly direct the analysis, and control which paths it visits first. Analyses written in a layered manner deliver results of interest to the user in a short time, thus addressing the shortcomings of batch-style analyses. Layered analyses can be easily integrated in an Integrated Development Environment like the Eclipse IDE in a way that is more closely interacting with the code developer.
Lisa Nguyen presented her research at the Student Research Competition of the »37th annual ACM SIGPLAN conference on Programming Language Design and Implementation« (PLDI). PLDI was held from 13-17 June 2016 in Santa Barbara, California, United States.
PLDI is the premier conference in the field of programming languages, covering the topics of design, implementation, theory, and efficient use of programming languages. ACM’s Student Research Competition is an internationally recognized venue enabling undergraduate and graduate students to present research results and exchange ideas with other students, judges, and conference attendees. It spans over several premier conferences (such as PLDI, ICSE, CHI or FSE) where students present their research, first as an abstract, then, as a poster, and finally, in a presentation. The first graduate and undergraduate students selected at each conference are then invited to participate in the Grand Finals of the following year. Lisa Nguyen scored first place in the graduate category.
Cross-posted from Secure Software Engineering
 We are still looking for one to two postdoctoral researchers to complement our research group at Paderborn university. For further information, please
We are still looking for one to two postdoctoral researchers to complement our research group at Paderborn university. For further information, please  We are happy to announce, that a paper on our new algorithm for demand-driven context- and flow-sensitive points-to analysis, called Boomerang, has been accepted at the ECOOP 2016 conference.
We are happy to announce, that a paper on our new algorithm for demand-driven context- and flow-sensitive points-to analysis, called Boomerang, has been accepted at the ECOOP 2016 conference. We are happy to announce, that a paper on our new algorithm for demand-driven context- and flow-sensitive points-to analysis, called Boomerang, has been accepted at the ECOOP 2016 conference.
We are happy to announce, that a paper on our new algorithm for demand-driven context- and flow-sensitive points-to analysis, called Boomerang, has been accepted at the ECOOP 2016 conference. Attending
Attending 




